1. Introduction
Welcome to a rolling blog series of my writeups for the Practical Malware Analysis labs that everyone and their mum has done. Note, I’ll mostly be using different tools to that of the book for efficiency, practice and to keep things interesting.
I’ll discuss the tools I use and my justification as I come to it in the labs. Without further ado, let’s get started.
2. Lab 1-1
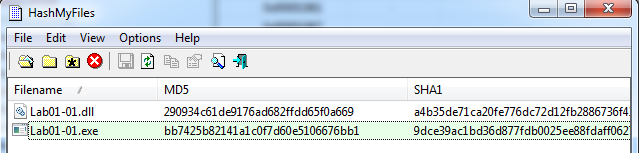
| File Name | MD5 Sum |
|---|---|
| Lab01-01.dll | 290934c61de9176ad682ffdd65f0a669 |
| Lab01-01.exe | bb7425b82141a1c0f7d60e5106676bb1 |
2.1. Question 1
Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
For this series I have used the VirusTotalUploader with my own API key to upload the files quickly. All that’s required is dragging-and-dropping into the app for a VTotal submission.
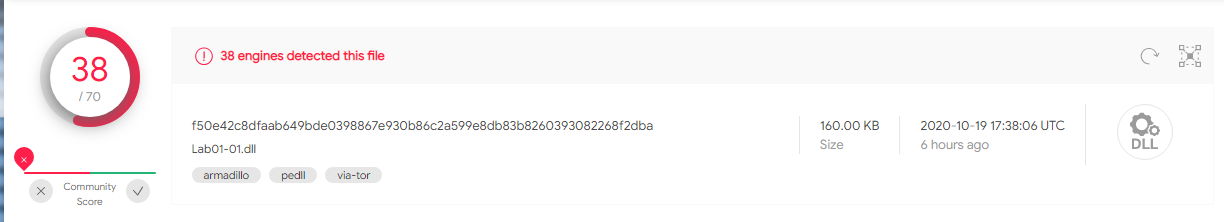
Lab01-01.dll
A: Yes, 38/70
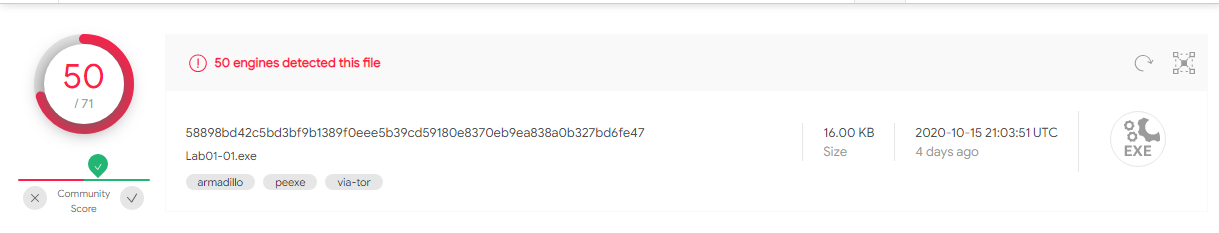
Lab01-01.exe
A: Yes, 50/70
2.2. Question 2
When were these files compiled?
For this I used the neat tool PEStudio to grab the PE file compile timestamps.
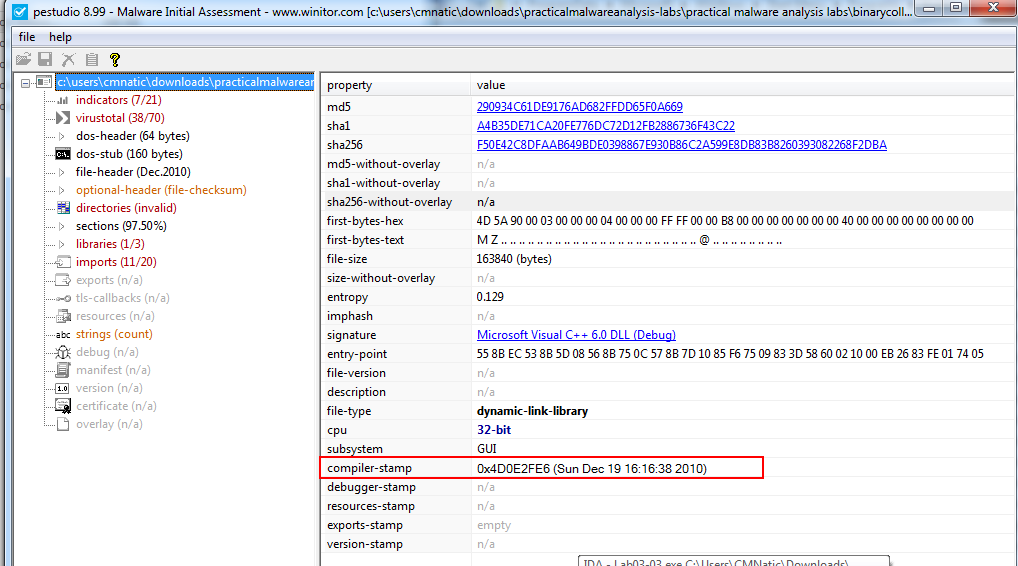
Lab01-01.dll
A: Sun Dec 19 16:16:38 2010
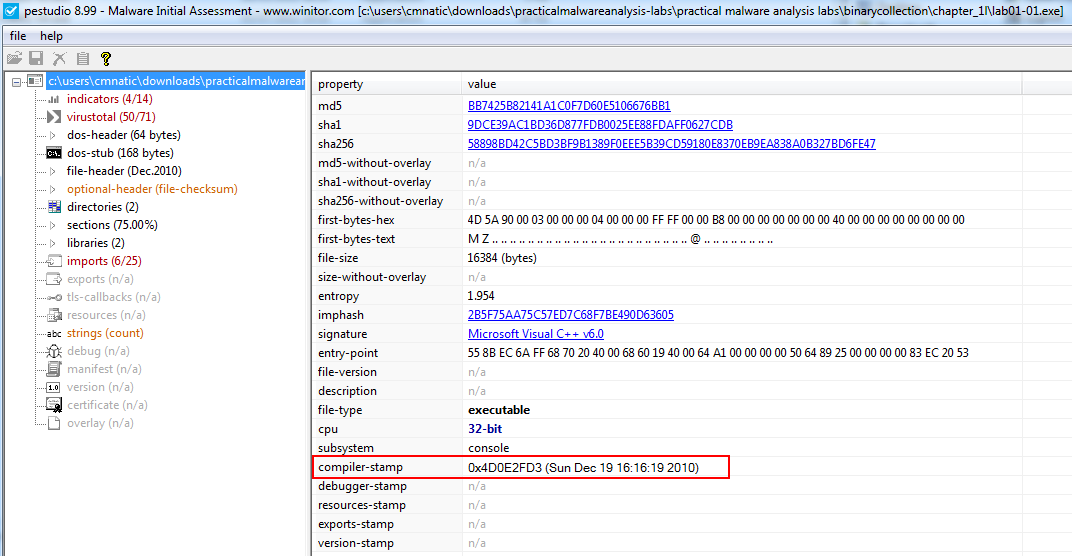
Lab01-01.exe
A: Sun Dec 19 16:16:19 2010
2.3. Question 3
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
There are a few ways of looking for indications of packing. For example using a tool like PEiD that is capable of detecting the signatures of packers like UPX amongst many more. However, inspecting the file’s imports and strings is usually a good indicator as to whether or not a file is obfuscated or packed in anyway.
n the screenshot below we can see a reasonable amount of imports for lab01-01.exe that are indicative of it’s behaviour such as CreateFileA
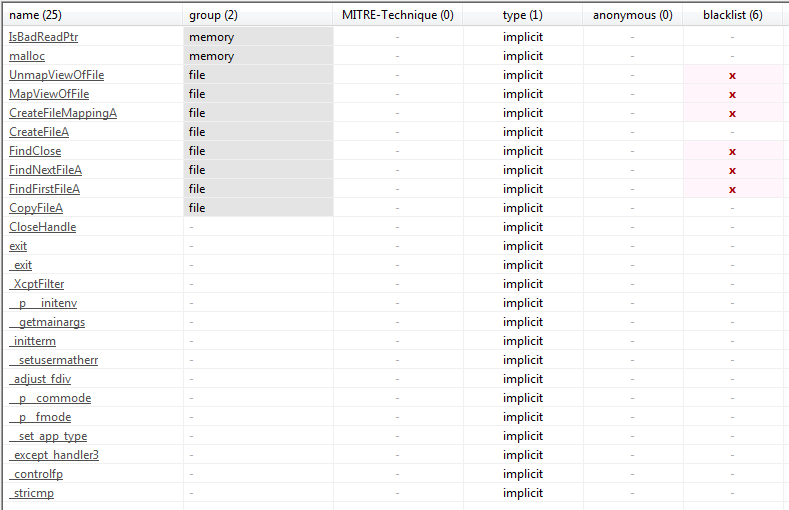
2.3.1. Lab01-01.dll
A: There are no indications of packing or obfuscation
2.3.2. Lab01-01.exe
A: There are no indications of packing or obfuscation
2.4. Question 4
Do any imports hint at what this malware does? If so, which imports are they?
2.4.1. Lab01-01.dll
A: The following imports are interesting to observe:
| Name of Import | Indicative Behaviour |
|---|---|
| CreateMutexA | DLL creates a mutex so that no more then one instance of the service can execute. This is common for malware such as ransomware to prevent files from being encrypted twice. |
| OpenMutexA | DLL accesses created mutex |
| Sleep | The DLL may way a certain amount of time for a certain condition/event to occur before it begins executing, or to perhaps evade sandboxing by adding a delay. |
2.4.2. Lab01-01.exe
A: The following imports are interesting to observe:
| Name of Import | Indicative Behaviour |
|---|---|
| FindFirstFileA | EXE may be looking for files in a directory |
| FindNextFileA | EXE may be looking for files in a directory |
| CreateFileA | EXE is capable of creating files on the system (confirmed by CreateFileMappingA) |
2.5. Question 5
What host- or network-based indicators could be used to identify this malware on infected machines?
2.5.1. Lab01-01.dll
A: As a process is created on execution, if the service was started, we could expect to see a process by the name of svchost.exe to be running on the infected host.
2.5.2. Lab01-01.exe
A: The executable calls reference to kerne132.dll. Note the 1 in place of l in kernel32.dll. This is an intentional spelling mistake to disguise the .dll as the legitimate kernel32.dll
2.6. Question 6
What network-based indicators could be used to find this malware on infected machines?
2.6.1. Lab01-01.dll
A: When inspecting the strings, we can see an IP address of 127.26.152.13 contained within the program. This could be a C2C server or a IP address for a dropper. The EXE may communicate with this, so we can look for it with network analysis.
2.6.2. Lab01-01.exe
A: There are no obvious network indicators of compromise.
2.7. Question 7
What would you guess is the purpose of these files?
2.7.1. Lab01-01.dll
A: The .dll setups a socket to send and receive data to an external host. This could be a botnet or creating some form of backdoor by contacting a C2C server.
2.7.2. Lab01-01.exe
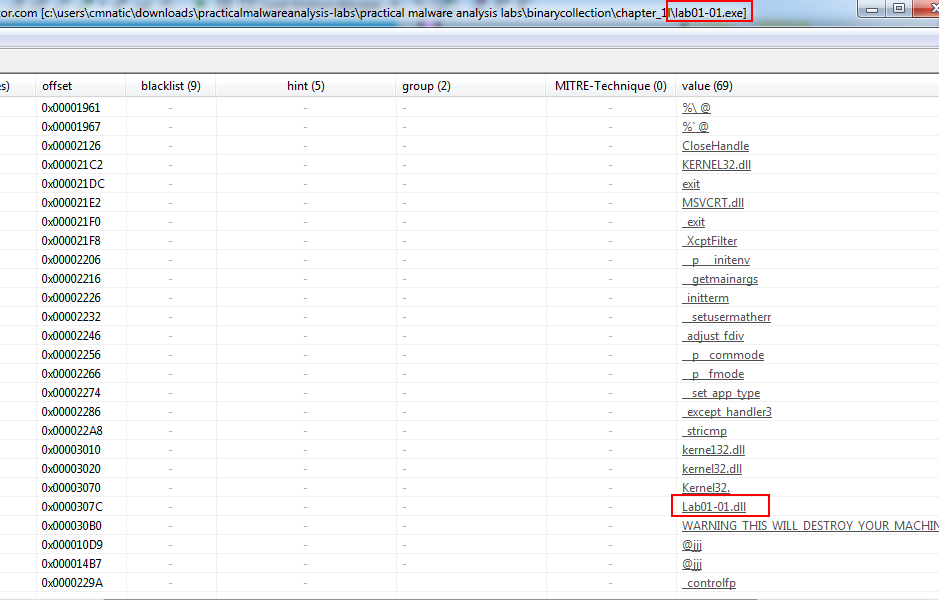
A: After inspecting the strings, the executable makes a reference to lab01-01.dll. The executable could be used to start the .dll as .dll’s cannot be executed like a normal .exe file.
3. Lab 1-2
| File Name | MD5 Sum |
|---|---|
| Lab01-01.exe | 8363436878404DA0AE3E46991E355B83 |
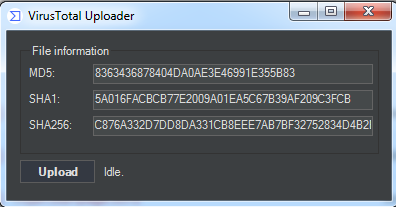
3.1. Question 1
Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
A: Yes, 48/69
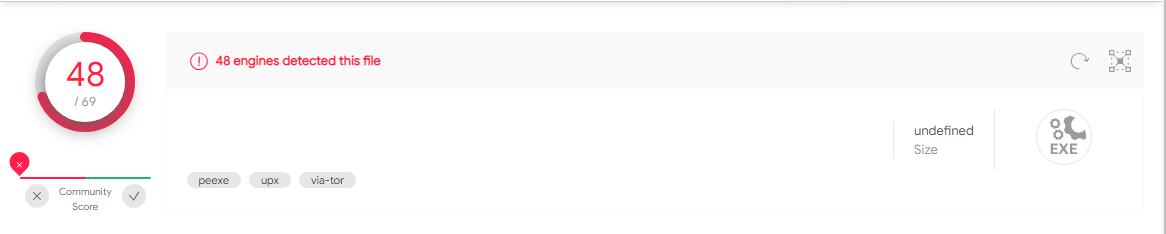
3.2. Question 2
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
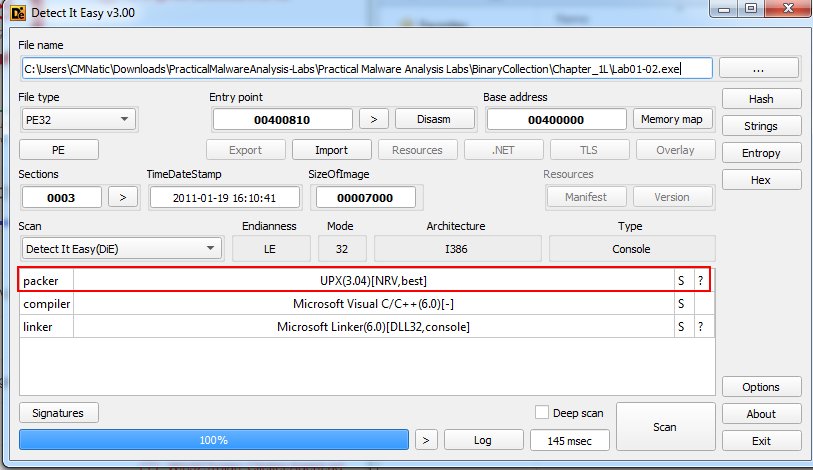
For this I used “Detect it Easy”
A: Yes, “Detect it Easy” detects the “UPX 3.04” packer being used.
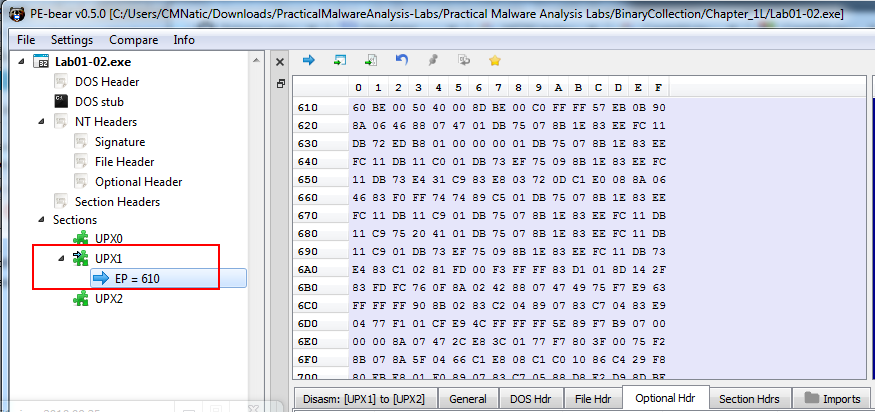
We can simply download UPX and use it to unpack this executable, where we can use “PE Bear” to verify that the file’s entrypoint is indeed a UPX section (specifically UPX1):
upx.exe –o Lab01-02-unpacked.exe –d Lab01-02.exe
3.3. Question 3
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
A: Imports worthy of note:
| Name of Import | Indicative Behaviour |
|---|---|
| InternetOpenA | EXE is capable of connecting to connect to a remote host |
| InternetOpenUrlA | EXE is capable of connecting to connect to a remote host |
| CreateServiceA | EXE is able to create a service that can be used for persistence on the infected host |
3.4. Question 4
What host- or network-based indicators could be used to identify this malware on infected machines?
A: The service “MalService” is created on the infected host, with a domain name of “http://www.malwareanalysisbook.com” which could be a C2C server and we may expect network traffic to and from this host.